System Files: 7 Essential Secrets Revealed for Ultimate Power
Ever wondered what keeps your computer running smoothly behind the scenes? It’s not magic—it’s system files. These hidden heroes manage everything from booting up to running apps, and understanding them can give you ultimate control over your device.
What Are System Files and Why They Matter
System files are the backbone of any operating system. They are critical components that ensure your computer boots up, runs applications, manages hardware, and maintains stability. Without them, your device would be nothing more than an expensive paperweight.
The Core Definition of System Files
System files are pre-installed files created by the operating system (OS) developer—such as Microsoft, Apple, or Linux distributors—that enable the OS to function properly. These files include executables, libraries, configuration files, and drivers that work together to manage system resources.
- They are typically hidden from regular users to prevent accidental deletion or modification.
- Examples include
ntoskrnl.exein Windows,kernel panichandlers in macOS, andvmlinuzin Linux. - They often reside in protected directories like
C:WindowsSystem32or/usr/bin.
“System files are the silent architects of your computer’s performance—working invisibly but indispensably.” — TechOps Journal, 2023
Types of System Files by Function
Not all system files serve the same purpose. They can be categorized based on their role within the operating system:
- Kernel Files: The core of the OS, managing memory, processes, and hardware communication. Example:
ntkrnlmp.exein Windows. - Dynamic Link Libraries (DLLs): Shared libraries used by multiple programs. Example:
kernel32.dll. - Configuration Files: Store system settings. Example:
boot.iniorregistry hivesin Windows. - Device Drivers: Enable hardware interaction. Example:
dxgkrnl.sysfor graphics. - Boot Files: Essential for startup. Example:
bootmgrandBCD(Boot Configuration Data).
Understanding these types helps users recognize which files are safe to interact with and which should be left untouched.
How System Files Work Behind the Scenes
The operation of system files is a symphony of coordination between software and hardware. When you press the power button, a chain reaction begins, orchestrated by these files.
The Boot Process and System Files
The journey from power-on to desktop involves several stages, each dependent on specific system files:
- BIOS/UEFI Initialization: The firmware checks hardware and locates the bootloader.
- Bootloader Execution: Files like
bootmgrandwinload.exeload the Windows kernel. - Kernel Initialization:
ntoskrnl.exestarts core services and loads drivers. - Session Manager:
smss.exeinitializes the user session and startswinlogon.exe. - Logon Process: The GUI appears, and user-specific settings are applied.
This entire sequence relies on the integrity of system files. A single corrupted file can halt the process, leading to boot failures or blue screens.
Role in Memory Management and Process Scheduling
Once the system is running, system files continue to manage resources. The kernel, for instance, uses ntoskrnl.exe to allocate memory and schedule processes efficiently.
- Virtual memory is managed through
pagefile.sys, a system file that extends RAM using disk space. - The scheduler ensures fair CPU time distribution among running applications.
- Interrupt handling is performed by system drivers to respond to hardware signals instantly.
These operations happen in milliseconds, invisible to the user but vital for smooth performance.
Common System Files in Windows, macOS, and Linux
Each operating system has its own set of critical system files. Knowing them helps in troubleshooting and understanding system behavior.
Windows: The Heart of NT Architecture
Windows, built on the NT kernel, relies heavily on a suite of system files located primarily in C:WindowsSystem32.
- ntoskrnl.exe: The Windows kernel, responsible for process and memory management.
- hal.dll: Hardware Abstraction Layer, allowing the OS to interact with different hardware setups.
- lsass.exe: Local Security Authority Subsystem Service, handles password changes and security policies.
- services.exe: Manages background services like Windows Update and Print Spooler.
- svchost.exe: Hosts multiple Windows services in shared processes.
Microsoft provides tools like System File Checker (SFC) to scan and repair corrupted system files.
macOS: Unix-Based Stability
macOS, derived from BSD Unix, uses a hybrid kernel called XNU (X is Not Unix). Its system files are stored in /System/Library and /usr.
- launchd: Replaces traditional init systems, managing daemons and services.
- kernel: The XNU kernel, handling low-level operations.
- dyld: Dynamic linker, loads shared libraries for applications.
- System Integrity Protection (SIP): Protects critical system files from modification, even by root users.
Apple enforces strict file protection, making macOS less prone to system file tampering compared to other systems.
Linux: Open-Source Flexibility
Linux distributions vary, but they share common system file structures based on the POSIX standard.
- vmlinuz: The compressed Linux kernel image.
- initrd or initramfs: Temporary root file system used during boot.
- systemd: Modern init system managing services and boot processes.
- /etc/fstab: Configuration file defining disk mounts.
- /proc and /sys: Virtual file systems providing kernel and hardware information.
Because Linux is open-source, users can inspect and modify system files—though doing so requires caution and root privileges.
Dangers of Corrupted or Missing System Files
When system files become corrupted, missing, or altered, the consequences can range from minor glitches to complete system failure.
Symptoms of System File Damage
Recognizing the signs early can prevent catastrophic failures:
- Slow boot times or failure to start.
- Blue Screen of Death (BSOD) with error codes like
0x0000007E(SYSTEM_THREAD_EXCEPTION_NOT_HANDLED). - Applications crashing unexpectedly.
- Missing or unresponsive system services.
- Corrupted desktop or login screen.
These symptoms often point to issues with critical files like ntdll.dll or win32k.sys.
Common Causes of Corruption
Several factors can lead to system file damage:
- Malware Infections: Viruses and ransomware often target system files to disable security or gain persistence.
- Improper Shutdowns: Power outages or forced reboots during file writes can corrupt data.
- Hardware Failures: Bad sectors on a hard drive can render files unreadable.
- Failed Updates: Windows or macOS updates that don’t complete properly may leave files in an inconsistent state.
- User Tampering: Deleting or modifying system files without understanding their role.
According to a 2022 report by AV-Test Institute, over 350,000 new malware samples are detected daily, many of which target system integrity.
How to Repair and Restore System Files
Luckily, modern operating systems come with built-in tools to diagnose and fix system file issues.
Using SFC and DISM in Windows
Windows provides two powerful command-line tools:
- System File Checker (SFC): Scans and repairs protected system files.
- Deployment Image Servicing and Management (DISM): Repairs the Windows image that SFC relies on.
To run SFC:
Open Command Prompt as Administrator
sfc /scannow
If SFC fails, use DISM:
DISM /Online /Cleanup-Image /RestoreHealth
After DISM completes, run SFC again. This two-step process resolves most file corruption issues.
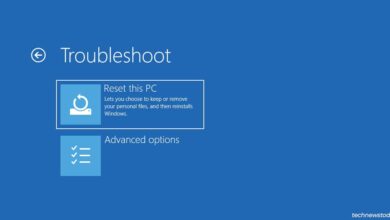
macOS Recovery Mode and First Aid
macOS users can boot into Recovery Mode (hold Cmd+R during startup) and use Disk Utility’s First Aid to repair disk and file system errors.
- First Aid checks the integrity of system volumes and repairs logical errors.
- Reinstalling macOS from Recovery does not erase user data but replaces system files.
Due to SIP, even if files are corrupted, they can often be restored without third-party tools.
Linux: fsck and Package Managers
Linux administrators use fsck (file system check) to repair disk-level issues:
sudo fsck /dev/sda1
For missing or corrupted system files, package managers like apt (Debian/Ubuntu) or dnf (Fedora) can reinstall them:
sudo apt install --reinstall linux-image-generic
This ensures that only verified, signed packages replace damaged files.
Best Practices for Protecting System Files
Prevention is always better than cure. Implementing strong security and maintenance habits can keep system files intact.
Enable System Protection Features
Modern OSes include built-in safeguards:
- Windows Defender and Firewall: Block unauthorized access and malware.
- System Integrity Protection (macOS): Prevents even root users from modifying protected files.
- SELinux or AppArmor (Linux): Enforce mandatory access controls.
Ensure these features are enabled and updated regularly.
Regular Backups and System Restore Points
Creating restore points allows you to roll back to a stable state if system files are compromised.
- In Windows, use System Protection to enable restore points.
- Use Time Machine on macOS to back up the entire system.
- On Linux, tools like
rsyncorTimeshiftcan create snapshots.
Backups should be stored on external drives or cloud services to survive hardware failures.
Avoid Unauthorized Software and Modifications
Third-party tweaks, cracks, or registry cleaners often modify system files in dangerous ways.
- Only install software from trusted sources.
- Avoid ‘system optimizers’ that promise speed boosts—many are scams.
- Never disable UAC (User Account Control) permanently.
A 2021 study by Kaspersky found that 30% of malware infections originated from pirated software.
Advanced Tips: Monitoring and Managing System Files
For power users and IT professionals, deeper control over system files can enhance performance and security.
Using Resource Monitor and Process Explorer
Windows includes Resource Monitor and Microsoft’s free Process Explorer to see which processes are using system files.
- Process Explorer shows DLLs loaded by each process.
- You can identify rogue software injecting into system processes.
- It highlights unsigned drivers that may be malicious.
This level of visibility is crucial for diagnosing performance bottlenecks or security breaches.
File Integrity Monitoring (FIM) Tools
Organizations use FIM tools like OSSEC, Wazuh, or Tripwire to detect unauthorized changes to system files.
- These tools create cryptographic hashes of critical files and alert on changes.
- They are essential for compliance with standards like PCI-DSS or HIPAA.
- Can be configured to auto-restore files or block suspicious processes.
For personal use, lightweight tools like WinAudit can perform similar checks.
Understanding File Permissions and Ownership
System files have strict permissions to prevent unauthorized access.
- In Windows, use
icaclsto view and modify permissions. - In Linux,
chmodandchowncontrol access. - Never grant full control to the
Everyonegroup on system files.
Misconfigured permissions can lead to security vulnerabilities or system instability.
Future of System Files: Trends and Innovations
As technology evolves, so do the nature and management of system files.
Immutable Operating Systems
New OS designs like Windows Core OS and Linux distributions such as Fedora Silverblue use immutable file systems.
- System files are read-only and cannot be modified during runtime.
- Updates are applied atomically—either fully succeed or roll back.
- Enhances security and stability by preventing tampering.
This model is gaining traction in enterprise and containerized environments.
Cloud-Based System Images
With the rise of cloud computing, system files are increasingly stored and managed remotely.
- Services like Azure Virtual Desktop or Amazon WorkSpaces stream OS images to devices.
- System files are maintained on servers, reducing local vulnerabilities.
- Instant rollback to clean images is possible.
This shift reduces the burden on end-users and improves security posture.
AI-Powered System Health Monitoring
Artificial intelligence is being integrated into system maintenance.
- Windows 11 already uses AI to predict disk failures and optimize performance.
- Future systems may auto-detect and repair corrupted files before they cause issues.
- AI can analyze file access patterns to detect zero-day attacks.
Companies like Microsoft and Google are investing heavily in this space.
What are system files?
System files are essential components of an operating system that manage hardware, software, and core functions like booting, memory management, and security. They are critical for the stable operation of any computer.
Can I delete system files to free up space?
No, you should never manually delete system files. Doing so can cause your operating system to become unstable or unbootable. Use built-in tools like Disk Cleanup instead.
How do I fix corrupted system files in Windows?
Use the System File Checker (SFC) tool by running ‘sfc /scannow’ in an elevated Command Prompt. If that fails, run DISM to repair the Windows image first.
Are system files the same across all operating systems?
No, each OS has its own set of system files. Windows uses NT-based files like ntoskrnl.exe, macOS uses Unix-derived files like launchd, and Linux uses open-source components like vmlinuz and systemd.
Why are system files hidden by default?
They are hidden to protect them from accidental deletion or modification by users. Changing or removing these files can lead to system crashes or security vulnerabilities.
System files are the invisible foundation of your digital experience. From the moment you power on your device to the seamless operation of your apps, these files work tirelessly behind the scenes. Understanding their role, protecting them from corruption, and knowing how to repair them when issues arise empowers you to maintain a healthy, high-performing system. As technology advances, the way we manage system files will continue to evolve—becoming more secure, automated, and resilient. Whether you’re a casual user or a tech professional, respecting the power of system files is key to mastering your device.
Further Reading: