System Group: 7 Powerful Insights You Must Know
Ever wondered how complex organizations manage their operations seamlessly? The secret often lies in a well-structured system group. This behind-the-scenes powerhouse drives efficiency, security, and scalability across industries.
What Is a System Group and Why It Matters

The term system group might sound technical, but its implications stretch far beyond IT departments. At its core, a system group refers to a collection of users, processes, or devices organized under a unified administrative framework to streamline access, permissions, and resource management within a computing or organizational environment. Whether in enterprise software, operating systems, or cloud platforms, system groups are foundational to maintaining order and control.
Defining System Group in Technical Terms
In computing, a system group is a logical grouping of user accounts or system processes that share common access rights and permissions. For example, in Unix-like operating systems such as Linux, system groups are used to manage file access and execute specific system-level tasks. A user assigned to the sudo group can perform administrative commands, while those in the www-data group might have access to web server files.
- System groups are created during OS installation or by administrators.
- They help enforce the principle of least privilege.
- Each group has a unique Group ID (GID) recognized by the kernel.
“System groups are the silent architects of access control in modern operating systems.” — Linux Foundation
System Group vs. User Group: Understanding the Difference
While both system groups and user groups organize accounts, their purposes differ significantly. User groups are typically created for collaboration—like a marketing team sharing documents. In contrast, system groups are often reserved for system-level functions and services. For instance, the daemon group runs background processes, not human users.
- User groups serve collaboration; system groups serve functionality.
- System groups often have restricted login capabilities.
- Membership in system groups should be audited regularly for security.
The Role of System Group in Operating Systems
Operating systems rely heavily on system groups to maintain stability and security. From Linux to Windows, these groups define who can do what, ensuring that only authorized entities interact with critical system resources.
System Groups in Linux and Unix Environments
Linux distributions use system groups extensively. During installation, the OS creates essential groups like root, bin, sys, and adm. These are not for regular users but for system daemons and administrative tools. For example, the adm group allows members to view log files in /var/log, crucial for troubleshooting.
- Common system groups:
daemon,lp(printing),mail,ssh. - System groups often have GIDs below 1000 to distinguish them from user groups.
- Administrators can modify group membership using the
usermodorgpasswdcommands.
For deeper insight, check the official Linux Foundation documentation on user and group management.
Windows System Groups and Security Identifiers
Windows takes a different approach with system groups, using Security Identifiers (SIDs) instead of numeric GIDs. Built-in groups like Administrators, SYSTEM, and Authenticated Users control access to system resources. The SYSTEM account, for instance, has the highest privileges and runs core OS processes.
- Local system groups are managed via Computer Management or PowerShell.
- Domain-level groups are handled through Active Directory.
- Improper configuration can lead to privilege escalation vulnerabilities.
“Misconfigured system groups are among the top causes of internal security breaches.” — Microsoft Security Response Center
System Group in Enterprise IT Infrastructure
In large organizations, system groups extend beyond individual machines to encompass entire networks, cloud environments, and identity management systems. They become a cornerstone of IT governance and operational efficiency.
Active Directory and Group Policy Management
Microsoft Active Directory (AD) uses system groups to enforce policies across thousands of devices. By assigning users to specific system groups, administrators can deploy software, restrict access, and audit activity uniformly. For example, a Finance-Systems group might have access to accounting software while being blocked from development tools.
- Group Policy Objects (GPOs) are linked to system groups.
- Nested groups allow for hierarchical permission structures.
- Best practice: Use role-based access control (RBAC) when defining groups.
Learn more about AD best practices at Microsoft Learn.
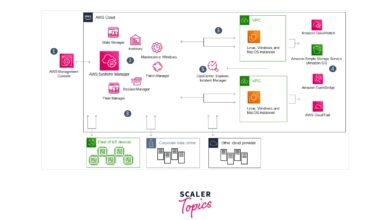
Cloud-Based System Groups in AWS and Azure
Cloud platforms like Amazon Web Services (AWS) and Microsoft Azure have redefined system groups through Identity and Access Management (IAM). In AWS, IAM groups are collections of users with attached policies that define permissions. Similarly, Azure uses Role-Based Access Control (RBAC) to assign roles to groups.
- AWS IAM groups simplify permission management for EC2, S3, and Lambda.
- Azure AD groups sync with on-premise directories for hybrid environments.
- System groups in the cloud support multi-factor authentication and conditional access.
“Cloud system groups are the gatekeepers of digital assets in the modern enterprise.” — AWS Security Blog
Security Implications of System Group Management
Poorly managed system groups can become a security liability. Unauthorized access, privilege creep, and dormant accounts in critical groups are common attack vectors exploited by cybercriminals.
Common Security Risks with System Groups
One of the most prevalent risks is over-permissioning—assigning users to powerful system groups like sudo or Administrators without justification. This violates the principle of least privilege and increases the attack surface.
- Orphaned accounts in system groups after employee departure.
- Excessive use of shared service accounts.
- Lack of regular group membership audits.
According to a CISA report, 80% of data breaches involve privilege misuse, often linked to misconfigured system groups.
Best Practices for Securing System Groups
To mitigate risks, organizations should adopt a proactive approach to system group governance. This includes regular reviews, automated provisioning, and logging of group changes.
- Implement Just-In-Time (JIT) access for elevated groups.
- Use tools like Microsoft Identity Manager or Okta for lifecycle management.
- Enable logging and alerting for group membership changes.
“Security isn’t a feature—it’s a process, and system group management is a critical checkpoint.” — NIST Cybersecurity Framework
System Group in Software Development and DevOps
In modern software development, system groups play a vital role in CI/CD pipelines, containerization, and infrastructure-as-code (IaC). They ensure that only authorized services and personnel can deploy or modify code.
Role of System Groups in CI/CD Pipelines
Continuous Integration/Continuous Deployment (CI/CD) systems like Jenkins, GitLab CI, and GitHub Actions use system groups to control who can trigger builds, access secrets, or deploy to production. For example, only members of the deploy-prod system group should have access to production deployment keys.
- System groups integrate with OAuth and SSO providers.
- Permissions are often defined in YAML configuration files.
- Audit trails should record which group member initiated each deployment.
System Groups in Docker and Kubernetes
Containerized environments rely on system groups for process isolation and security. In Docker, the --group-add flag allows containers to run with specific group privileges. Kubernetes uses Role-Based Access Control (RBAC) to define which users or service accounts belong to system-level roles like cluster-admin.
- Kubernetes namespaces often have associated system groups.
- Pod security policies can restrict group IDs allowed in containers.
- Service accounts in Kubernetes are automatically assigned to system groups.
Explore Kubernetes RBAC documentation at kubernetes.io.
How to Create and Manage a System Group
Creating a system group requires careful planning and execution. Whether on a local machine or in the cloud, the process involves defining purpose, assigning members, and enforcing policies.
Step-by-Step Guide to Creating a System Group in Linux
Creating a system group in Linux is straightforward using command-line tools. Here’s how:
- Open a terminal with root or sudo access.
- Run
sudo groupadd --system devopsto create a system group nameddevops. - Add a user with
sudo usermod -aG devops john. - Verify with
groups johnor check/etc/group.
The --system flag ensures the group is created with a low GID, marking it as a system group.
Managing System Groups in Windows Server
On Windows Server, system groups are managed through the Local Users and Groups console or PowerShell. To create a new system group:
- Open Computer Management → Local Users and Groups → Groups.
- Right-click and select “New Group.”
- Name it (e.g.,
App-Support) and add members. - Assign permissions via Security tab on file or folder properties.
PowerShell command: New-LocalGroup -Name "App-Support" -Description "Support team for internal apps".
Future Trends in System Group Management
As technology evolves, so does the concept of the system group. From AI-driven access control to decentralized identity systems, the future promises smarter, more adaptive group management.
AI and Machine Learning in Access Control
Emerging tools use AI to analyze user behavior and automatically adjust system group memberships. For example, if a developer rarely uses admin privileges, the system might suggest removing them from the sudo group.
- AI detects anomalies in group access patterns.
- Predictive analytics can prevent privilege escalation attacks.
- Tools like Microsoft Azure AD Identity Protection already use AI for risk assessment.
Zero Trust and System Groups
The Zero Trust security model assumes no user or device is trusted by default. System groups in a Zero Trust architecture are dynamic, context-aware, and short-lived. Access is granted based on identity, device health, and location—not just group membership.
- System groups are re-evaluated in real-time.
- Temporary group assignments replace permanent ones.
- Integration with identity providers like Okta or Ping Identity is essential.
“In a Zero Trust world, system groups are not static—they’re adaptive security boundaries.” — Google BeyondCorp Whitepaper
Case Studies: System Group in Action
Real-world examples illustrate how effective system group management can transform operations and security.
Healthcare Organization Secures Patient Data
A large hospital network implemented role-based system groups in Active Directory to control access to electronic health records (EHR). Nurses were placed in a Clinical-Staff group with read-only access, while administrators had full access via a separate group.
- Reduced unauthorized access incidents by 70%.
- Met HIPAA compliance requirements.
- Automated onboarding/offboarding using HR system integration.
FinTech Startup Scales with Cloud IAM
A fast-growing fintech company used AWS IAM groups to manage developer, QA, and production access. Developers could deploy to staging but required approval to join the prod-deployers system group.
- Prevented accidental production changes.
- Enabled rapid scaling without compromising security.
- Integrated with Slack for approval workflows.
What is a system group?
A system group is a logical collection of users, services, or devices grouped together to manage permissions and access rights in an operating system or network environment. It is used to enforce security policies and streamline administrative tasks.
How do I create a system group in Linux?
Use the command sudo groupadd --system groupname to create a system group. Then add users with sudo usermod -aG groupname username. The group will appear in /etc/group with a system-reserved GID.
What’s the difference between system groups and user groups?
System groups are intended for system processes and administrative functions, often with low GIDs and restricted logins. User groups are for collaboration among human users and typically have higher GIDs.
Why are system groups important for security?
They enforce the principle of least privilege, reduce attack surface, and enable auditability. Misconfigured system groups are a common cause of privilege escalation and data breaches.
How are system groups used in the cloud?
In cloud platforms like AWS and Azure, system groups are implemented via IAM policies and RBAC roles. They control access to resources like virtual machines, databases, and storage buckets.
System group management is far more than a technical detail—it’s a strategic imperative. From securing sensitive data to enabling seamless collaboration in DevOps, system groups form the backbone of modern digital infrastructure. As organizations embrace cloud, AI, and Zero Trust models, the way we define and manage these groups will continue to evolve. The key is to stay proactive, audit regularly, and align group policies with business needs and security standards. Whether you’re a system administrator, developer, or CISO, understanding the power of the system group is essential for building resilient, scalable, and secure systems.
Further Reading: